2023 Edition: Digital Authentication and Identity Proofing in Public Benefits Applications
On May 19, 2023, the Digital Benefits Network published a new, open dataset documenting authentication and identity proofing requirements across online SNAP, WIC, TANF, Medicaid, child care (CCAP) applications, and unemployment insurance applications.

Overview
Agencies that administer public benefits applications online continually balance multiple potentially conflicting priorities around privacy, fraud prevention, and accessibility to ensure equitable outcomes. As we started our research on digital identity in public benefits, we quickly learned that there was not a single, publicly available, source of information documenting digital authentication and identity practices across public benefit program applications. By releasing this dataset, we aim to make it easier to quickly understand the landscape of digital authentication and identity proofing practices currently in use across core public benefits programs, including:
- Supplemental Nutrition Assistance Program (SNAP)
- Temporary Assistance for Needy Families (TANF)
- Medicaid
- Special Supplemental Nutrition Program for Women, Infants, and Children (WIC)
- Child Care Assistance (CCAP)
- Unemployment Insurance (UI)
Driving this project and our research on digital identity generally is our concern about online application requirements and implementations of identity proofing that create additional burdens for applicants, potentially block benefits seekers from applying for or receiving benefits, duplicate processes across programs, and raise challenging issues around privacy and data security. We are also concerned that the advocacy around recent technology implementations has been an all or nothing approach to remove a type of technology, rather than supporting government practitioners in navigating solutions to produce equitable outcomes.
On this page you will find:
Open Data
- Authentication and proofing practices across six benefits programs
- Data and analysis for each program
Analysis
Research Goals & Process
Feedback & Engagement
Project Background & Potential Next Steps
- When the Digital Benefits Network launched our digital identity research agenda in December 2022, we knew it would be essential to get a comprehensive, up-to-date, understanding of the identity proofing and authentication requirements that benefits seekers may encounter.
- On February 28, 2023, the Digital Benefits Network published an open dataset documenting authentication and identity proofing requirements across online unemployment insurance (UI) applications in the 53 states and territories that administer this program, based on publicly available information.
- On May 19, 2023, following a collaboration with Code for America as part of their Benefits Enrollment Field Guide project, we also released similar data for online applications across five additional benefits programs.
- Going forward, the Digital Benefits Network will continue engagement with government agencies, advocates, technology implementers, and others in the ecosystem to identify and promote best practices in online benefits applications and digital services.
Open Data
Digital Authentication and Identity Proofing Across Benefits Programs Dataset: Spreadsheet
Digital Authentication and Identity Proofing Across Benefits Programs Dataset: Gallery
This Airtable view displays data about authentication and identity proofing practices in online SNAP, TANF, Medicaid, WIC, child care, and unemployment insurance applications across states and territories. You can use filters to view data for specific programs and jurisdictions, or to highlight different variables. Program-specific views are also available below.
Program-Specific Data and Analysis
As noted above, many states have combined online applications that allow residents to apply for multiple programs within one application. Although many of the applications in this dataset are linked and the dataset documents applicants’ experiences when applying for all available core programs, we also wanted to provide program-specific views of this data to help users quickly review trends within individual programs. Below, we link to six program-specific pages, each of which includes a program-specific view of the dataset in spreadsheet and gallery formats, program-specific visualizations, and program-specific summaries of authentication and identity proofing trends.
(e.g., all applications that include SNAP)
(e.g., all applications that include TANF)
(e.g., all applications that include Medicaid MAGI)
(e.g., all applications that include WIC)
Child Care (CCAP) Data and Analysis →
(e.g., all applications that include Child Care)
Unemployment Insurance Data and Analysis →
(all UI applications, always stand alone)
Cross-Program Analysis
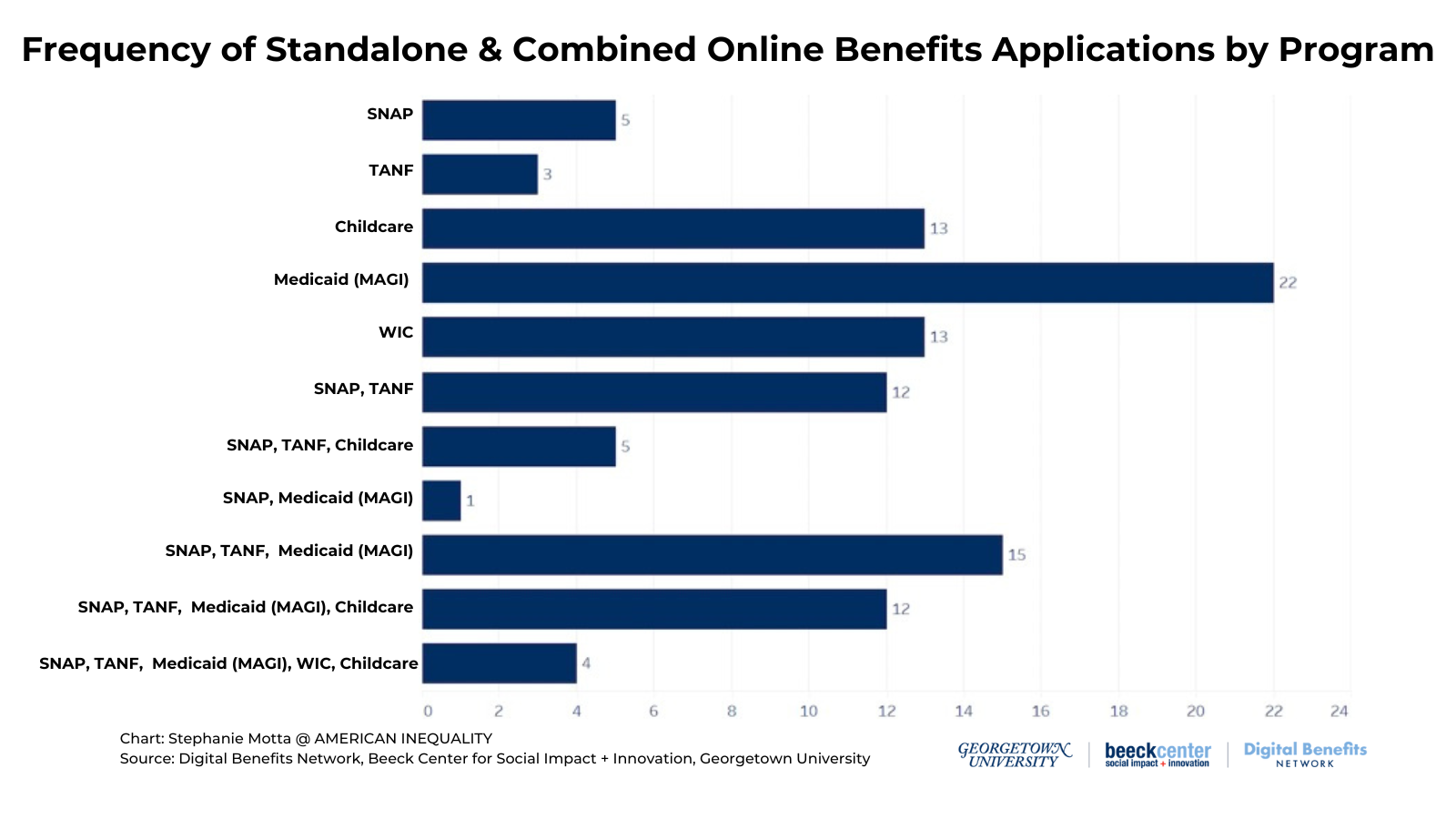
For this project, we collected data about authentication and identity proofing practices used for online applications of six federally-funded, state-administered programs: SNAP, TANF, Medicaid, WIC, child care, and unemployment insurance applications across states and territories. The final dataset includes 158 applications.
Outside of UI applications, many of the applications we reviewed for SNAP, WIC, TANF, Medicaid, and child care are combined applications that allow users to apply for more than one benefit program at a time. (Code for America’s web page for their Benefits Enrollment Guide visualizes combined applications by state/territory.) Our data documents which programs a person would see as included on an application. We recognize that on the backend, state agencies may have different definitions for integrated or combined applications.
The data we captured represents applicant experiences when applying to all benefits available on a single application flow (e.g., MAGI Medicaid + SNAP + TANF). In some cases, if a user applies for only SNAP or only MAGI Medicaid their experience may be slightly different than what we’ve documented here. We decided to approach data collection this way both for practicality and also to document the most comprehensive experience possible for each application flow.
Some states also have multiple applications for the same programs (e.g., SNAP/TANF in Mississippi or SNAP/TANF/Medicaid in California), or offer simplified, stand-alone SNAP applications in addition to combined applications (e.g., kynect in Kentucky, or North Carolina’s ePASS). In instances that states have multiple applications that cover the same programs, we have selected one application to include on map visualizations, typically deferring to the application that includes the most benefits programs.
In our data collection, we targeted online enrollment processes for Modified Adjusted Gross Income (MAGI)Medicaid. As context, the Center for Budget and Policy Priorities (CBPP) explains that federal rules require states to allow MAGI-eligible groups to submit applications and forms online or via telephone, but these rules do not currently require similar simplified processes for non-MAGI populations. (Non-MAGI pathways for Medicaid eligibility are based on old age or disability). We encountered several cases where non-MAGI Medicaid was included on the same portal as MAGI Medicaid or alongside other benefits applications. During our data collection process, however, we noticed that it was sometimes difficult to ascertain whether a given portal allowed users to apply for non-MAGI Medicaid. For this reason we did not include non-MAGI Medicaid as a benefits category in the published dataset at this time.
As we continue to gather feedback and update our datasets, the numbers below may change. The points we make should be understood as general observations to help users quickly make sense of this dataset.
Cross-program Snapshots
Authentication
A majority of applications across programs require applicants to log in or create an account to access applications.
- 118 applications in this dataset, or 75%, require applicants to log in or create an account before they can start an application.
- Another 14 applications make it optional for users to log in or create an account before applying.
- 15 applications do not appear to use account registration at any point in the application process. A smaller number of applications (11) don’t require users to create accounts before beginning an application. However, these 11 applications do prompt users to create accounts during the application process or to come back to their applications later.
- Of the 143 applications that require or allow account creation, either to start an application or later in the process, 93 of those account registration processes require users to include an email address.
- Among applications that require users to create an account to start an online application, 75 out of 118 (64%) require an email address as part of the account creation process.
- 31 applications are using single sign-on options (SSOs) that enable applicants to use the same login for other government services in the state.
- 6 applications prompt users to log in to an application portal with credentials from another service such as Facebook, Google, or ID.me.
- We found evidence that 117 applications (81%) that have a log in requirement or option offered some kind of authentication security measures such as multi-factor authentication or email validation links.
Requirements to create accounts vary between programs.
- Compared to applications for other programs, applications for WIC are less likely to require account registration to start an application. Applications for UI most often require account registration to start an application.
- Email address requirements are more common as part of required account registration processes for UI applications as compared to other programs.
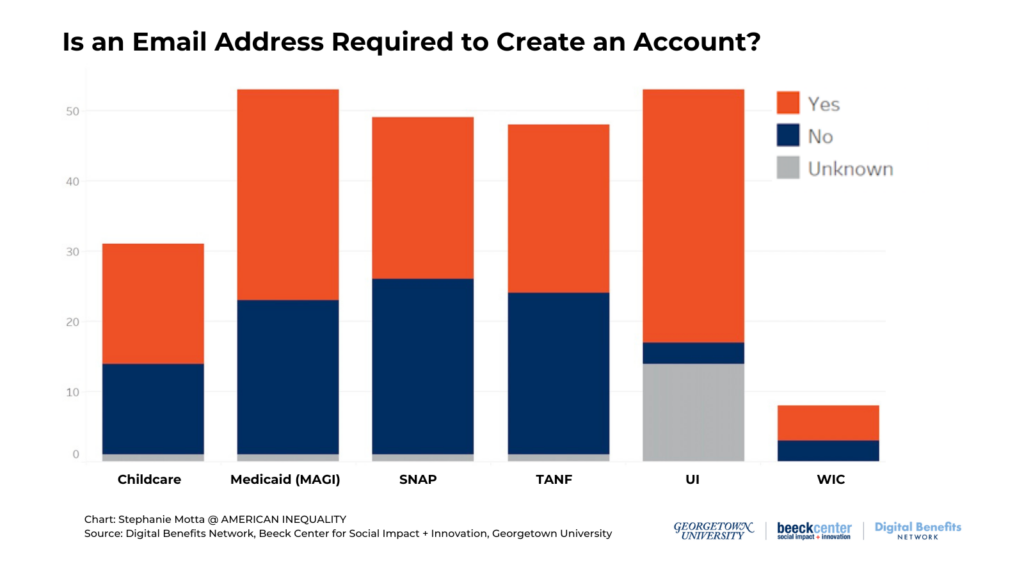
This chart shows often applications that include particular benefits programs require an email address as part of an account registration process.
Identity Proofing
Across the dataset, around a third of applications require or prompt some type of active identity proofing steps as part of an online application process.
- 59 online applications in the cross-program dataset require or prompt some type of active or front-end identity proofing steps for some or all applicants. (See below for more on our definitions of active or front-end identity proofing steps and variations between programs.)
- 37 applications require active or front-end identity proofing steps for all applicants.
- In 17 of these applications, identity proofing steps are placed before an applicant initiates an application. In 13 of these applications identity proofing steps are incorporated during an application. For five UI applications that appear to require identity proofing, it’s unclear when that takes place. One other UI application–Iowa’s –, prompts claimants to verify their identity during the application process, but if they decline or are unsuccessful they must verify later. In another UI application (Nebraska), claimants must take steps to demonstrate their identity after filing.
- 17 applications present identity proofing steps as optional, meaning a user can immediately skip the prompt or, if their identity cannot be verified online, applicants can still continue the online application process.
- Of these applications, nine prompt identity proofing steps before an applicant initiates an application, seven prompt identity proofing steps during the application process. For one application it was not clear when identity proofing takes place.
- We also found five UI applications where it appeared that identity proofing might be used for some, but not all claimants.
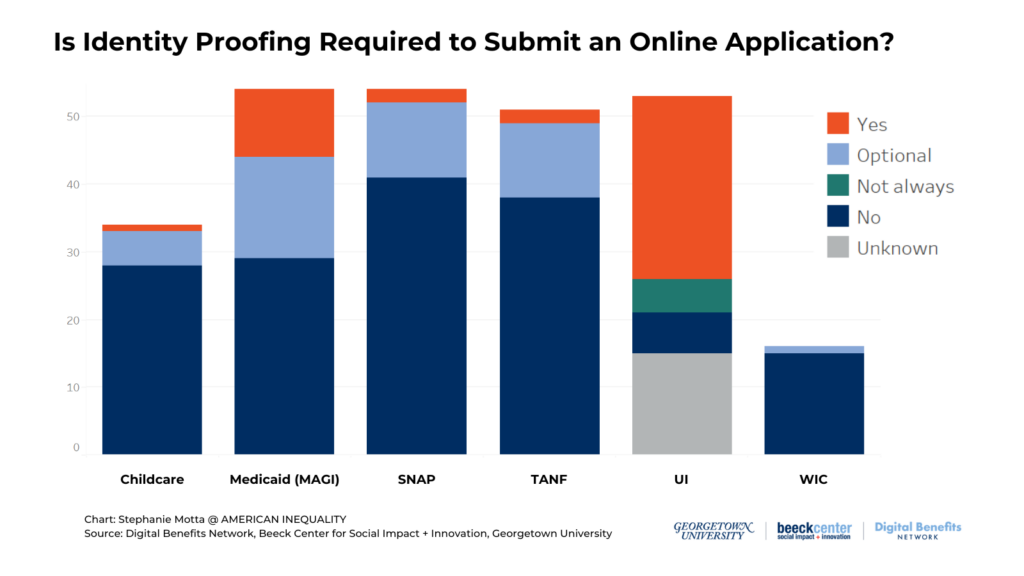
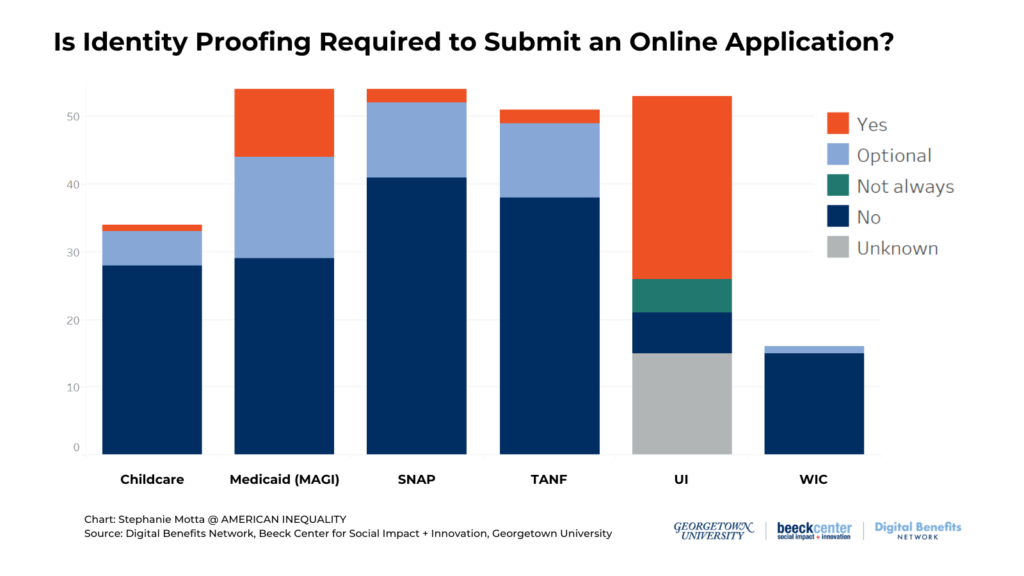
This chart shows how often applications that include particular benefits programs prompt or require active identity proofing actions to apply online. As the chart shows, identity proofing prompts are most common in applications that include MAGI Medicaid and Unemployment Insurance.
Across the safety net, the use of identity proofing requirements and prompts varies across programs.
- Identity proofing requirements were most common in unemployment insurance online applications. Just over half of UI applications require some type of active identity proofing steps to apply.
- Among other safety net programs, identity proofing requirements or prompts were most common for applications that allow users to apply for MAGI Medicaid. We found 46% of applications that include MAGI Medicaid require or prompt identity proofing steps.
- Identity proofing prompts were least common for WIC applications. Only one WIC application, Michigan’s combined MI Bridges application for SNAP, TANF, Medicaid, WIC, and child care, prompts optional identity proofing.
Identity proofing methods also vary between UI applications and other safety net applications.
- We found evidence that 22 labor agencies were using biometrics for identity proofing. These were coded in the dataset as ID Document Upload plus Video/live selfie to emphasize the experience that claimants encounter rather than backend processes. One other agency, Tennessee, prompts some claimants to upload a photo of themselves holding an identity document. It was not clear whether this step is required for some or all claimants, when during the claim filing process that might happen, or whether those images are being reviewed manually or through automated software.
- We did not find evidence that biometrics are currently being used for identity proofing in any other safety net programs. When identity proofing prompts or requirements are included in online SNAP, TANF, WIC, Medicaid, or Child care applications, they appear to use knowledge-based verification (KBV).
Personal Information Requested or Required
Applications present requirements or requests to submit personally identifiable information (PII) such as a Social Security Number (SSN) in different ways.
- We are also interested in what types of PII users are required or asked to submit during an application process, separate from any requirements or prompts to upload identity documents. For many benefits programsincluding Medicaid, TANF, SNAP, and UI benefits, applicants are required to provide SSNs as a condition of eligibility. However, federal agencies have provided important recommendations and guidance on the collection of SSN in online applications in some programs. For example, the U.S. Department of Agriculture’s Food and Nutrition Service has stated that online SNAP applications are required to allow users to proceed through the application process without being required to submit their SSN.
- Federal agencies have also highlighted how requests for or requirements to provide SSNs for non-applicant household members can create access barriers for U.S. citizen children and other eligible individuals concerned about disclosing immigration status and SSNs for family members not seeking assistance.
- In our data collection, we were interested in documenting how requests and requirements to provide an SSN are presented to applicants seeking benefits rather than non-applicant household members during an online enrollment process.
- This data is most relevant at a program level. On the program specific pages linked to below, we detail findings about how fields requesting SSN are presented to applicants applying for all available core safety net programs in a given application (e.g., SNAP or SNAP + TANF or SNAP + TANF + MAGI Medicaid ).
- We document when SSN is a required field within an application. We also document when SSN is a required field if a user indicates they have an SSN, when it may be possible to submit online without disclosing an SSN (e.g., the field is not required but it also is not presented as “optional” for applicants, and the system may allow users to move through the form without disclosing an SSN), when it’s explicitly optional, and when SSN is not requested.
Across programs:
- SSN is required in 62 applications (primarily UI applications).
- SSN is required if a user indicates they have one in 13 applications (primarily applications that include MAGI Medicaid).
- In 55 applications, SSN is not explicitly optional but it appears possible for an applicant to move through the online application and submit online without disclosing their SSN.
- In ten applications — primarily child care applications – SSN is explicitly optional or recommended.
- In 17 applications, including 13 WIC applications or pre-applications and 4 child care applications, SSN is not requested.
- In one application, we could not determine based on the data we had access to whether SSN was required or not.
- Driver’s license number or state ID number was required or requested in 27 unemployment insurance applications. It was only required or requested in two other safety net applications.
This chart shows how often applications that include particular benefits programs request or require applicants to disclose their Social Security Numbers (SSN) during an online application process.
Identity Proofing Vendors
The identity proofing vendor landscape is different in UI applications as compared to other benefits applications.
- For unemployment insurance applications, the most common named identity proofing vendor was ID.me. This vendor appears to be the current identity proofing vendor for at least 20 state workforce agencies, and has worked with additional states in the past. We found evidence that four state labor agencies (Iowa, Kansas, Rhode Island, and Wisconsin) are using LexisNexis Risk Solutions for KBV, although other research suggests this number is likely higher.
- Among other safety net programs, Experian was the most common identity proofing vendor (observed for 21 applications).
- We hope to continue building out this data on identity proofing vendors used in safety net applications. Within the methodology of this project, we primarily relied on publicly available information, information on application flows, statements on agency websites, and in some cases news coverage. Additional information could be pulled through deeper time-intensive reviews of state contracting repositories and other methods.
Vendors for Benefits Systems/Portals
There are a few companies that state agencies hire to build benefits systems/claimant portals for UI. We have less information in this dataset about contractors used in other safety net systems.
- For unemployment insurance applications, we found information for many labor agencies about private vendors involved in developing the agency’s benefits system/claimant portal, and have included that data on the UI specific data page. Given differences in our research protocols, we have less information on vendors who built benefits portals for other programs, but this is a piece of data we would be interested in building out in future.
The Impact of Login and Identity Proofing on Benefits Access
Agencies that administer public benefits applications online continually balance multiple potentially conflicting priorities around privacy, fraud prevention, and accessibility to ensure equitable outcomes.
When we launched our digital identity research agenda in December 2022, we knew it would be essential to get a comprehensive, up-to-date, understanding of the identity proofing and authentication requirements that benefits seekers may encounter. Driving this project and our research on digital identity generally is our concern about online application requirements and implementations of identity proofing that create additional burdens for applicants, potentially block benefits seekers from applying for or receiving benefits, duplicate processes across programs, and raise challenging issues around privacy and data security. We are also concerned that the advocacy around recent technology implementations has been an all or nothing approach to remove a type of technology, rather than supporting government practitioners in navigating solutions to produce equitable outcomes.
The Center on Budget and Policy Priorities and Code for America have previously suggested that removing login and identity proofing requirements may improve access to benefits programs. As was made clear during the pandemic, the design and implementation of online benefits applications and identity proofing approaches can significantly impact applicants’ ability to access essential benefits.
Identity proofing requirements and automated fraud detection incorporated into benefits applications may help prevent theft, but some solutions also create new challenges for eligible claimants. For example, automated fraud detection processes may be relatively frictionless for many users, but as explained in the U.S. Digital Response’s Identity Proofing for UI report and New America’s Playbook for Improving Unemployment Insurance Delivery, detection mechanisms, like flags on multiple claims submitted from the same address, may block rightful claimants and disproportionately affect marginalized communities.
While the overall data related to identity proofing obstacles is limited, there is evidence to suggest benefits administrators need to think carefully about how identity proofing steps are incorporated into benefits applications. In their work with the IRS Volunteer Income Tax Assistance (VITA) program, Code for America found that 88% of their clients halted the application process when they were asked to complete identity verification steps using an external portal.
Knowledge-based verification questions – sometimes also referred to as remote identity proofing or RIDP – can create obstacles for people with limited credit history, as well as immigrant parents applying for services on behalf of their children. Additionally, because of data breaches, answers to these types of questions, which include questions about cars owned, previous loans, or past addresses, may not actually be secret. The National Institute of Standards (NIST) has previously outlined limits on the use of KBV questions for identity proofing. In 2019, the Government Accountability Office also issued guidance recommending that several federal agencies discontinue using KBV practices and strengthen their identity proofing processes.
The use of biometric comparisons for identity verification, such as facial recognition software to evaluate a selfie against a government ID — a technique introduced by many state labor agencies during the pandemic and the IRS— can present accessibility and equity issues for individuals who are unable to successfully complete the process, and introduce potential for bias and disparate impacts. Such use cases also raise broader questions about privacyand transparency.
Following the release of this landscape data on authentication and identity proofing approaches, we are eager to continue working closely with state agencies and other partners to help agency leaders navigate tradeoffs in different approaches, map out key decision points around digital identity in public benefits, and promote best practices for privacy, fraud prevention, and accessibility.
Research Questions and Goals
In building this dataset on identity proofing and authentication practices across core benefits programs applications, we sought to address several questions, including:
- When and how do applicants need to create a log-in to apply for benefits online?
- What kinds of PII are applicants required or requested to share when applying online?
- When and how are front-end identity proofing steps incorporated into application processes?
- What identity proofing methods are applicants asked to use?
In building and releasing this dataset publicly, we hope to:
- Create an easy-to-consult and readily-updatable resource documenting the landscape of authentication and identity proofing practices benefits seekers may encounter.
- Make it easier for state and territorial agencies, advocates, technology implementers, and federal agencies to understand the digital identity landscape in public benefits.
- Expand our own understanding of the varied approaches to login and identity proofing across benefits administering agencies.
Research Process and Protocol
To answer our research questions, we independently collected details about unemployment insurance applications using publicly-available information about UI applications from agency websites, application portals, claimant guides, news coverage, vendor websites, and contracting repositories. We established a data sharing agreement and data collection partnership with Code for America to support its Benefits Enrollment Field Guide and facilitate our data collection about authentication and identity proofing in online SNAP, TANF, MAGI Medicaid, WIC, and child care applications. For these programs, we were able to access more information about the online applicant experience because Code for America’s protocol involved filling in benefits applications without submitting.
We chose these approaches—review of publicly available information about online UI applications and assessments of application flows for other programs—over other methods (e.g., surveys, interviews) to comprehensively capture point-in-time information about programs across states and territories. There are some natural limitations to this approach. Since we could not ask detailed questions of state agencies, there are some entries in the dataset that are incomplete. In these cases we have coded specific entries as “unknown.” However, we wanted to start with this approach to ensure that we could gather information about core safety net programs across all states and territories. We have already seen this data enriched and clarified by direct engagement with administering agencies, advocates, and other technology implementers. Going forward, we will continue to seek out opportunities to engage with state leaders and other partners on this topic.
Building this dataset involved reviewing applications and public-facing materials. It also required us to identify data points that would be most relevant for understanding authentication and identity proofing across applications based on our own understanding and conversations with stakeholders in our networks. For each of the data columns we attempted to encode information in ways that most accurately match what an applicant would encounter. For example, we’ve coded biometric identity proofing methods as “ID Document Upload” and “Video/live Selfie” rather than “Facial recognition technology” to emphasize what a claimant is asked to do. Additionally, for some entries, we had to make interpretations based on the information we could access.
Data Collection: UI Applications
Between October 1, and November 20, 2022, we reviewed publicly available information on unemployment insurance applications including agency websites, application portals, claimant guides, news coverage, vendor websites, and contracting repositories. For UI applications a valid SSN is often required early in the claims process. Because some labor agencies appear to immediately check the validity of SSNs entered, we decided to not enter false SSN information or other sample applicant data into these systems. We also did not register for accounts with these portals.
We spent approximately 75 to 90 minutes reviewing each labor agency’s unemployment compensation application during initial data collection and quality checks. After completing an internal review of the data in early December 2022, we shared this dataset with members of the UI Technology Coordinating Coalition for feedback and made small modifications based on member responses. When entering information into our dataset, we erred on the side of caution. This meant leaving fields blank or marking specific columns as “unknown” if there were contradictions or ambiguities in the information we found. We have also used the Public Notes column in the dataset to document those complexities and open questions. Since launching the UI dataset in February, we have continued to make small updates based on new information from state agencies and feedback.
Data Collection: SNAP, WIC, TANF, Medicaid, and Child Care Applications
To collect data on SNAP, WIC, TANF, Medicaid and child care applications we collaborated with Code for America(CfA) during data collection for their 2023 Benefits Enrollment Field Guide. Our team assisted with a select number of assessments for CfA’s project and established a data sharing partnership to access their data and share our own data focused on authentication and identity proofing. CfA’s protocol involved creating accounts (if required) and filling in applications with sample applicant data without submitting it. This gave us access to additional information and texture about the process of applying for SNAP, WIC, TANF, Medicaid, and child care online.
We built out this data for SNAP, WIC, TANF, Medicaid, and child care applications between October, 2022 and February, 2023. After inputting data, we conducted an internal review of each application entry in February and March of the same year to ensure accuracy and consistency. Our team spent approximately an hour working with each application. We have also used the “Public notes” column in the dataset to document complexities and open questions.
Notes on Data fields
Complete identity proofing is a multi-step process. This includes:
- Resolution, which involves confirming that the PII asserted by a person matches a single, real identity
- Validation, which means evaluating that identity evidence such as a driver’s license or other personal ID is genuine, correct, and related to a real person
- Verification, which establishes a link between a person claiming an identity and the identity information and evidence they provide.
During data collection, we wanted to differentiate between processes that cross-check user PII on the back-end, and active identity proofing steps that users must complete to successfully apply. For that reason, this dataset includes multiple data collection fields to capture information related to the identity proofing process and checks of identity data.
Additionally, our designations around identity proofing varied slightly between UI applications and the other program applications in this dataset. In both cases, we were primarily interested in remote identity proofing steps that applicants would be asked to complete when submitting benefits applications online. For UI, there were a few cases where we also documented identity proofing steps that may happen after applications are submitted, either online or through other channels such as in person or via postal mail. In contrast to programs like SNAP or WIC, which have an interview or appointment touchpoint before benefits are issued, we wanted to document these post-submission steps for UI applications where they appeared. This was because these might be the final steps needed for a claimant to receive their benefits. Additionally, for many non-UI applications, we found optional document uploaders, which were presented as pathways to streamline an application process. Because these were not presented as roadblocks and did not result in identity verifications online, we did not count those as active/front-end identity proofing prompts.
Additionally, for UI, because we were not filling out applications, we could not see whether a claimant who is unable to successfully verify their identity is given an option to proceed with the application and verify their identity later in the process. Thus, the data on UI applications documents where an identity proofing prompt or requirement appears in an application using publicly available information, we cannot necessarily account for what happens when that process fails.
Feedback and Engagement
We are publishing this dataset openly and publicly at this stage of our research to share knowledge and also to solicit feedback and engagement. We envision this dataset as a starting point, and hope that people who visit the dataset will help ensure the accuracy of the data, fill in any gaps, conduct their own analysis, and share ideas for further extensions of this work.
This data represents a point in time. We also know that the information we were able to access may not reflect the most up-to-date experiences of claimants, and that application requirements and processes can be complex. For that reason, this data is not meant to be a guide for claimants seeking benefits. This project also does not provide context on state level policies.
We welcome general or specific feedback about the data set or specific feedback about an application included in the dataset via our designated feedback form.
We are grateful for the feedback and input we have already received including from members of the Unemployment Insurance Technology Coordinating Coalition, and other stakeholders working on improvements to core safety net programs. We are eager to continue soliciting additional feedback.
We view this dataset as one step in our digital identity research agenda, which will help us direct further research and continued engagement with state and territorial agencies, technology implementers, and others in the ecosystem over the coming months. We encourage you to reach out to us at digitalbenefits@georgetown.edu if you have questions about our data or ideas for expanding or augmenting our research. To receive updates about our work we invite you to subscribe to the Digital Benefits Network.
Acknowledgments
- A special thanks to our colleagues at Code for America for the data sharing partnership that facilitated the development of these datasets, and for inviting us to support work on their Benefits Enrollment Field Guide.
- We would also like to thank Jeremy Ney and Stephanie Motta from American Inequality for creating the data visualizations that helped illustrate our learnings from this research in new ways.
- Finally, we would like to thank the partner organizations and state agencies that spoke with us about their work, both formally and informally.
Citation
Cite as:
Elizabeth Bynum Sorrell and Ariel Kennan, “Digital Authentication and Identity Proofing in Public Benefits Applications” Digital Benefits Network, May 19, 2023
Digital Authentication and Identity Proofing in Public Benefits Applications
Data Licensing
We’ve invested in making great data that’s open to use under Creative Commons Attribution 4.0 International (CC BY 4.0).
Want to make your own project? Go for it!
You are free to:
- Share: Copy and redistribute the material in any medium or format
- Adapt: Remix, transform, and build upon the material for any purpose, even commercially.
We ask that you provide Attribution — You must give appropriate credit, provide a link to the license, and indicate if changes were made.
Please get in touch if you have any questions related to accessing or using the data.